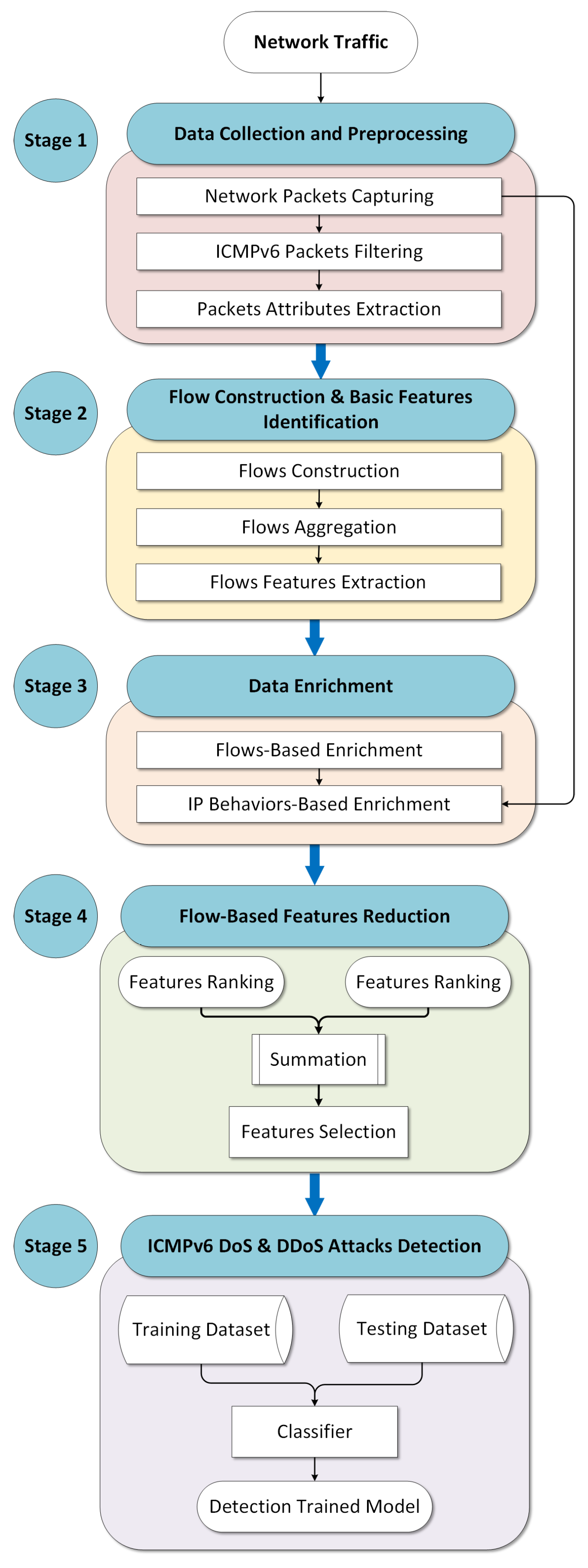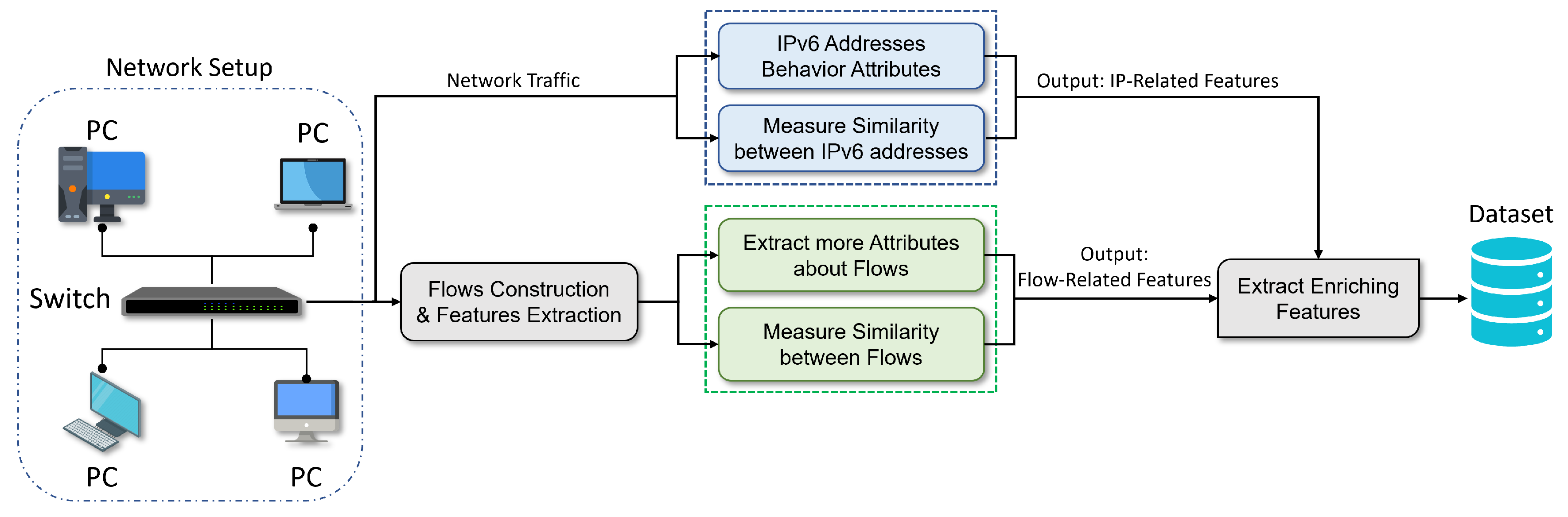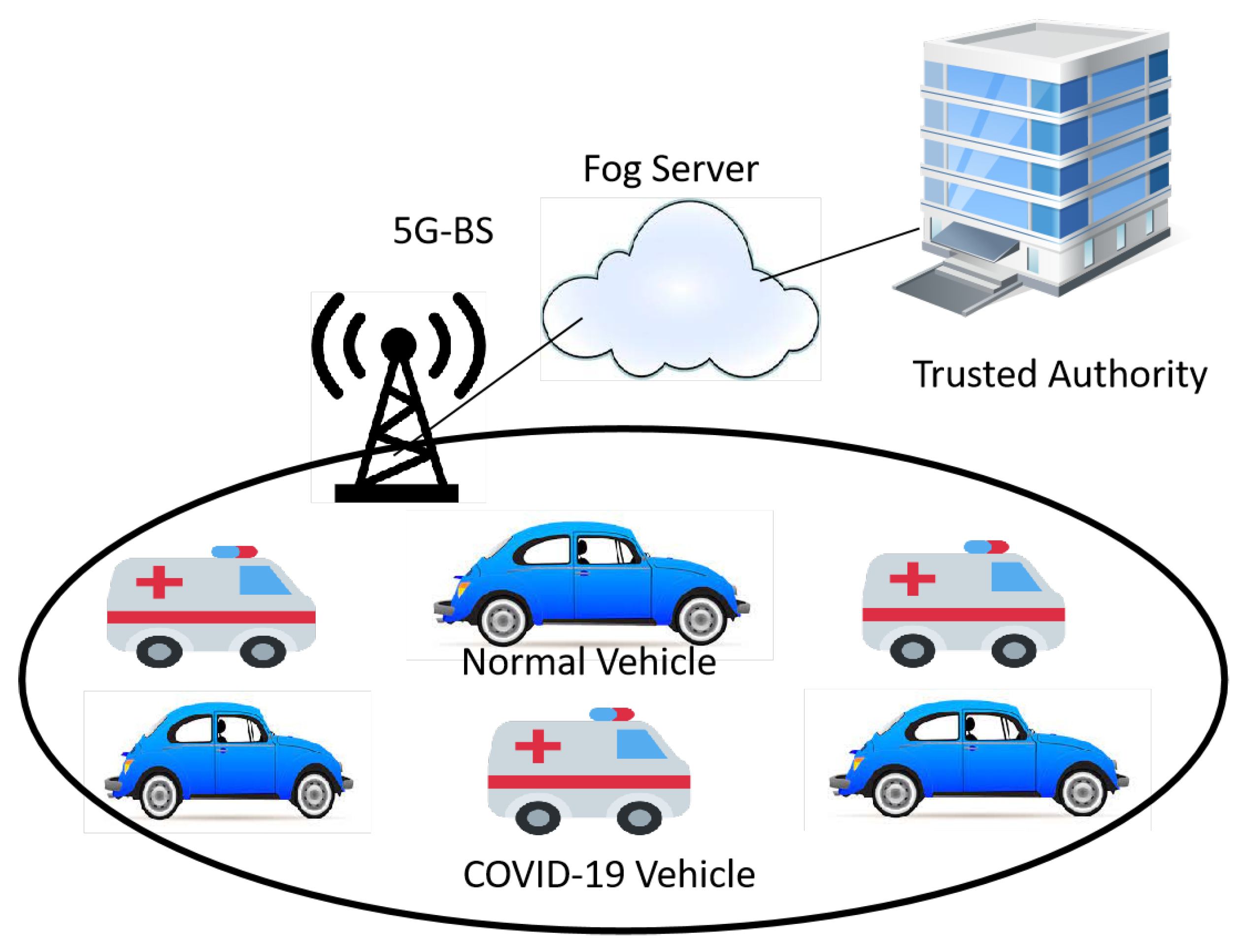
IJERPH | Free Full-Text | COVID-19 Vehicle Based on an Efficient Mutual Authentication Scheme for 5G-Enabled Vehicular Fog Computing
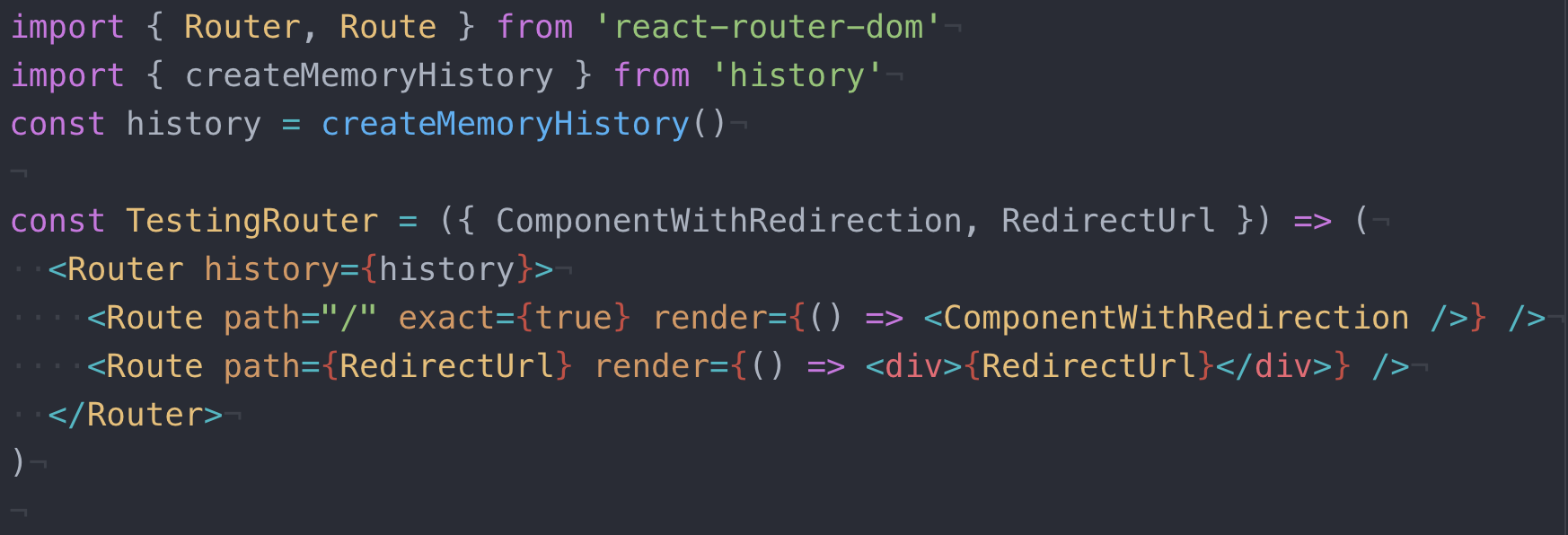
How to test <Redirect> from `react-router` with RTL (React Test Library) and JEST | by Ilya Zykin | Medium

Noroff School of technology and digital media added a cover video. | By Noroff School of technology and digital media | Facebook

USB Power Strip Surge Protector White Flat Plug 10ft Extension Cord 900j 10a240v for sale online | eBay

Amazon.com: ARRIS SURFboard SBG6580 DOCSIS 3.0 Cable Modem/ Wi-Fi N300 2.4Ghz + N300 5GHz Dual Band Router - Retail Packaging Black (570763-006-00) : Electronics

Whitelist: WI-FI PT / 4 - ATTACKS MAN-IN-THE-MIDDLE / 4.4 - Stealing username/passwords with SSL (Secure Socket Layer) MITM attack

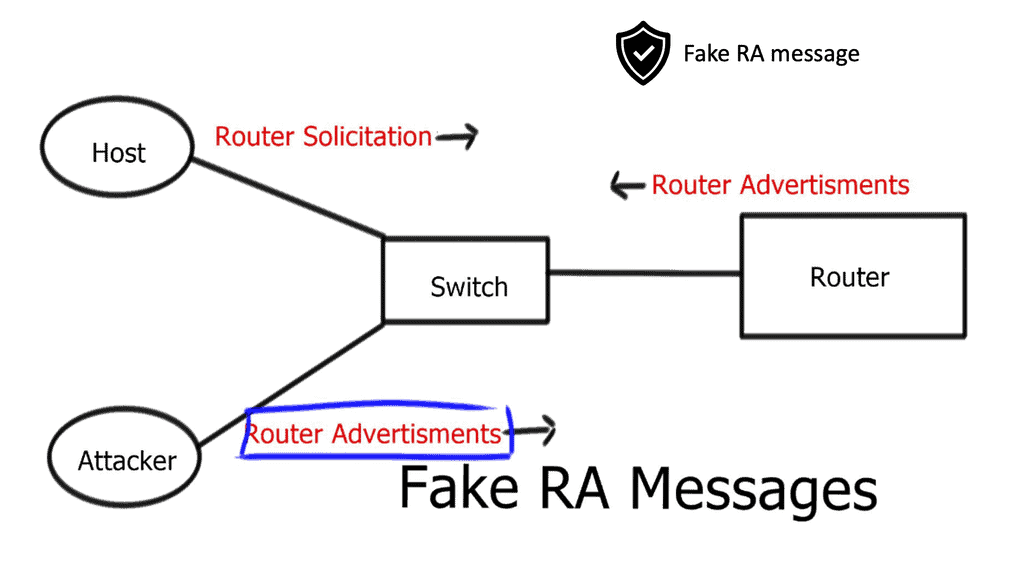
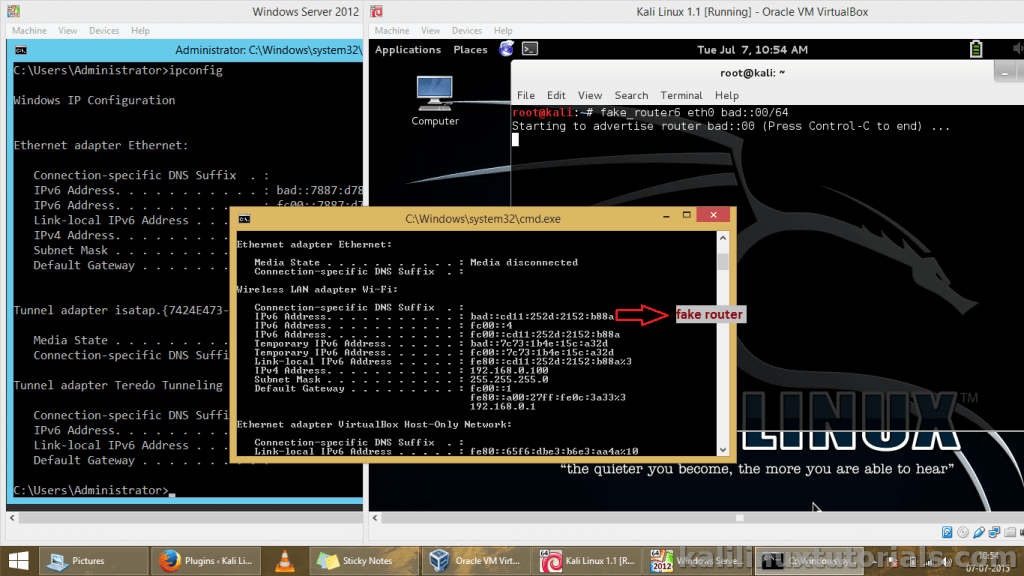
An Improved Secure Router Discovery Mechanism to Prevent Fake RA Attack in Link Local IPv6 Network | SpringerLink
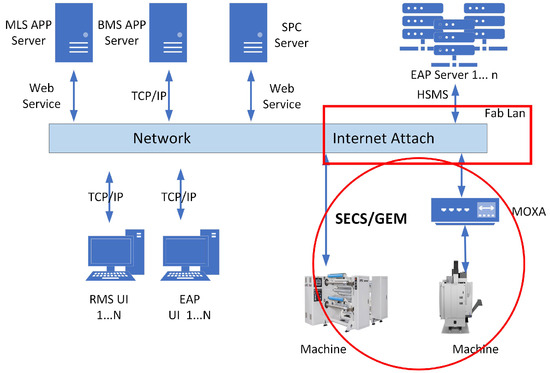
Sustainability | Free Full-Text | Replay-Attack Detection and Prevention Mechanism in Industry 4.0 Landscape for Secure SECS/GEM Communications

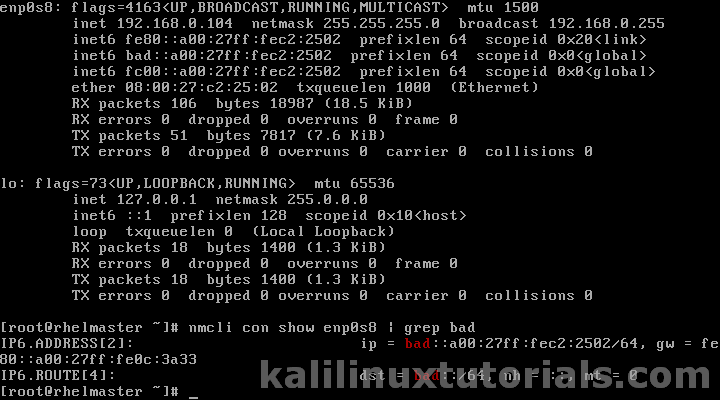








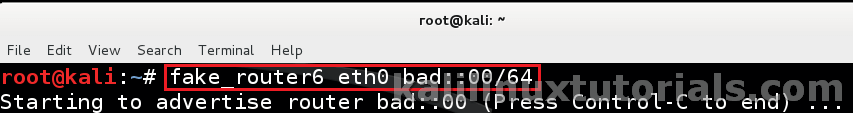


![PDF] A Study on Wireless Intrusion Prevention System based on Snort | Semantic Scholar PDF] A Study on Wireless Intrusion Prevention System based on Snort | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b00c58872ec57d443dffc0c58ef69eadd4641659/8-Figure11-1.png)